Why we need to care about API key?
11/4/20232 min read


Introduction
API (Application Programming Interface) keys are essential for accessing and utilizing various web services and applications. These keys grant developers access to specific functionality and data, allowing them to integrate their own software with external systems seamlessly. However, it is crucial to understand the risks associated with API keys being published in public repositories and the steps to prevent such incidents from occurring. There is an interesting article from GitGuardian where they did an intense research on some of the public repo. Here are some insights from the article
All the code committed to PyPI packages was analyzed (>450 000 projects).
3 938 total unique secrets found, with 768 valid credentials.
2 922 projects contained at least one unique secret.
Notable trends include a surge in leaked tokens and an increase in key leaks.
The prevalence of hardcoded credentials has become a leading cause of breaches in 2023.
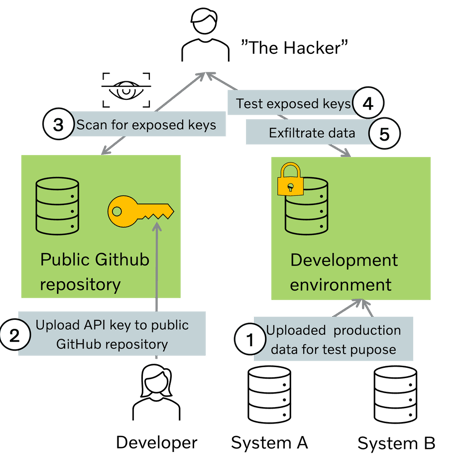
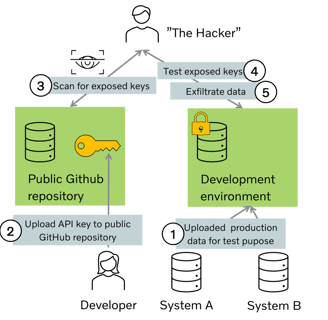
In the following diagram you can see what the attacker can do
The Risks of Exposing API Keys
When API keys are accidentally or intentionally exposed in a public repository, they become vulnerable to misuse by malicious actors. Here are some significant risks:
Unauthorized Access: Hackers can use exposed API keys to gain unauthorized access to sensitive data or perform actions on behalf of the key's owner.
Data Breach: Exposed API keys can lead to data breaches, compromising the confidentiality, integrity, and availability of sensitive information.
Financial Loss: Hackers may exploit exposed keys to incur financial losses by abusing paid services or making unauthorized transactions.
Reputation Damage: If an organization's API keys are exposed, it can result in reputational damage, loss of customer trust, and potential legal consequences.
Examples of API Key Misuse
Let's consider a practical example to understand the potential damage caused by exposing API keys:
Suppose a developer accidentally publishes their Google Maps API key on a public code repository. An attacker discovers this key and decides to exploit it. With the exposed API key, the attacker can:
Impersonate the Developer: The attacker can use the exposed API key to impersonate the developer, potentially accessing their personal information or hijacking their application.
Exceed Usage Limits: The attacker can abuse the API key to exceed usage limits, resulting in financial consequences for the developer.
Inject Malicious Code: By gaining access to the developer's application, the attacker can inject malicious code, leading to further security breaches or compromising user data.
Preventing API Key Exposure
To prevent API key exposure and mitigate the associated risks, consider the following preventive measures:
Use Environment Variables: Store API keys and other sensitive information in environment variables rather than hardcoding them in code repositories.
Implement Access Controls: Restrict API key access to specific IP addresses, domains, or authorized users only.
Regularly Rotate Keys: Rotate API keys periodically to minimize the impact of potential exposure.
Employ Encryption: Encrypt API keys and other sensitive data at rest and in transit to provide an additional layer of protection.
Follow Secure Development Practices: Educate developers about the importance of API key protection and enforce secure coding practices.
Encrypt credentials
Automated scanning in CI/CD chain
Conclusion
API keys are valuable assets that, when exposed, can lead to severe consequences such as unauthorized access, data breaches, financial loss, and reputational damage. By understanding the risks and implementing preventive measures, developers and organizations can ensure the protection of their API keys and the systems they integrate with.